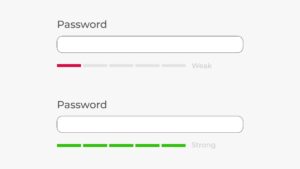
Password Complexity is a serious component of Cyber Security. Almost every device, tool or area of access requires a password of some kind to authenticate the user and grant permission to that which is being accessed. Brute Force
Letter from Anonymous: Earlier this morning, I received a call from “Amazon Fraud Protection” (that’s how they presented). I was told that pre-authorized purchases were being processed on my account and they had to verify my information. The caller proceeded to ask me about my travel and where I lived in the past and my … Read more
Beth Bean, Assistant Director for Integrated Operations at the Cybersecurity and Infrastructure Security Agency, wrote an article titled: “CELEBRATING SMALL BUSINESS WEEK: CYBERSECURITY HELP FOR SMALL BUSINESSES”.

Password Complexity is a serious component of Cyber Security. Almost every device, tool or area of access requires a password of some kind to authenticate the user and grant permission to that which is being accessed. Brute Force
A malware attack is when cybercriminals create malicious software that’s installed on someone else’s device without their knowledge to gain access to personal information or to damage the device, usually for financial gain.
It is tax season and every year we have an increase in cyber-crime regarding tax fraud.
W-2 phishing scams peak during tax season.
In 2020 during the height of Covid-19, Google fought against over 18 million daily malware and phishing email attacks related to the pandemic according to reports.
Taking advantage of people’s need for financial assistance, these scammers pose as a bank offering “forgivable business loans to individuals impacted by the pandemic.”
Eye-opening data around the impact of human error demonstrates how simple user mistakes can compromise your organization’s cybersecurity posture.
Just-released data from cyber insurer Coalition shows massive increases in both the frequency of ransomware attacks and the ransom demand with Maze and Ryuk leading the way.